Business Continuity vs. Disaster Recovery: Understanding the Differences

It can be tempting to live with the belief that a disastrous event happening to our business is highly unlikely. Always being prepared for the worst can seem like a waste of energy. Nonetheless, unfortunate events do happen, and when they do, it can have devastating effects if the company is not adequately prepared. Business […]
Are You Using the Right Data Storage Solutions for Your Business?

Data is one of the most essential assets for modern-day businesses, and it is increasingly important to manage your data properly. With such a large base of consumers, companies rely heavily on their data storage methods to ensure business continuity and scale their business. Because data is so important, finding the best data storage methods […]
What’s The Difference Between Data Center Redundancy 2N vs. N+1

Since the dawn of the modern computer age, data centers have been the foundation for building our computing facilities and networking equipment. Data centers are responsible for storing, collecting, processing, and distributing data. They represent any company’s backbone that relies on applications, networking services, or data to deliver products and services to its customers. Because […]
What You Need To Know About SolarWinds Orion Security Breach

Companies throughout the world use the latest technology and the internet to scale their businesses. The path to success is innovation and expansion; therefore, keeping up with the latest trends in terms of tech is going to make a massive difference down the road. Every successful company along the way had to build a solid […]
How Colocation Data Centers Services are Powering the Remote Workplaces

As of March 2020, the coronavirus pandemic forced many employees to either reduce their staff or seek remote solutions for their businesses. Remote workplaces are becoming a more common occurrence in many industries and amongst many types of employees. Even before the pandemic, a 2018 IWG survey suggests that 70% of professionals work remotely at […]
Backup vs. Disaster Recovery as a Service: Which Is Better for You and Why?

Businesses worldwide are reviewing their disaster recovery plans in the wake of COVID-19, and that includes checking in on your organization’s backup data essentials. While you probably have methods for preventing data loss due to human error, system malfunctions, or cybercrimes, you may not have been as prepared to protect your information during a pandemic. […]
Data Breaches Are A Growing Epidemic: No One Is Safe

For the past few years, there has been a constant stream of data breaches that have hit the headlines, ranging from the theft of medical information, account credentials, corporate emails, and internal sensitive enterprise data. When a data breach occurs, companies will usually haul in third-party investigators, notify regulators, promise to do better, and give […]
The Difference Between a Next Generation Firewall and a UTM Appliance

Data security remains the most critical cybersecurity issue on the map today. It’s now standard to employ some firewall type on every system, most commonly a next-generation firewall (NGFW). However, another multipurpose option is available: a unified threat management (UTM) appliance. With the increasing need for more secure and reliable systems, many companies seek high-end […]
Cryptographic Ransomware Removal And Protection With Volico Endpoint Protection
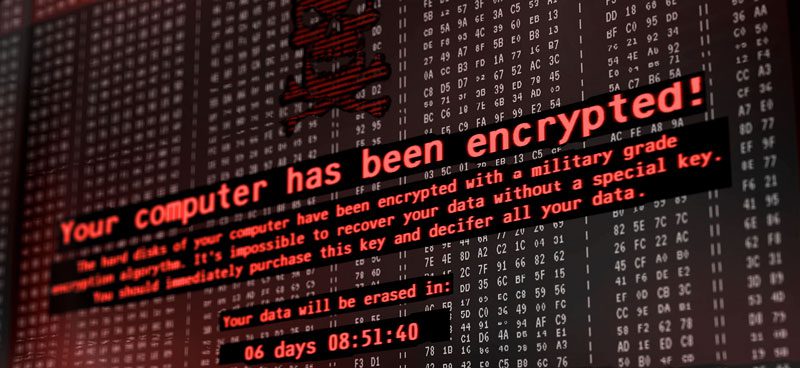
Crypto Ransomware is rampant. Most variants of it (CryptoLocker, TeslaCrypt) are malicious binary files that are very intelligent, aware of their surroundings, and highly polymorphic. Cryptographic ransomware that can morph on the fly makes it extremely difficult for standard signature-based antivirus programs to detect, as well as making it difficult to detect with “Anti-Malware” programs. […]
Why Can the Average Cost of a Data Breach reach into the Millions?

A data breach is, unfortunately, a common occurrence in 2019. Countless companies and governments around the world have suffered ransomware attacks and DDoS attacks that have left them helpless to deal with the damage at hand. It’s come to the point that these data breaches can cost companies millions of dollars in damages. There are multiple […]


