Backup vs. Disaster Recovery as a Service: Which Is Better for You and Why?

Businesses worldwide are reviewing their disaster recovery plans in the wake of COVID-19, and that includes checking in on your organization’s backup data essentials. While you probably have methods for preventing data loss due to human error, system malfunctions, or cybercrimes, you may not have been as prepared to protect your information during a pandemic. […]
Why Should a Business Invest in Clustered Server Environment

Nearly every business depends upon the internet for essential business procedures. Performance and downtime gaps symbolize reduced sales and productivity along with reputation, mitigation, and other expenses. The actual price of tech bugs and out-of-date technology can result in the loss of millions. For this reason, a huge and developing amount of businesses make a […]
Understanding Enterprise Unified Threat Management (UTM) and Next-Generation Firewall (NGFW)

Network security now is the most important thing to have for all businesses, no matter it’s a small SMB or a complicated enterprise. While researching network security solutions, companies are coped with various options from a solutions point of view for dealing with every threat to the solutions which merge services into a single appliance. […]
Data Center Cross Connect Explained

Organizations are more and more searching for collocation data centers to fulfill the networking requirements. IDG research states that around 65% of companies are already using third-party facilities as a part of their strategy, and the collocation model appears gaining velocity in the proceeding time. One of the fundamental causes of this trend is the […]
The Importance of Smart Hands Service During the Coronavirus Pandemic

Smart Hands Support A smart hands support is operational, 24/7 on-demand support for remote management, troubleshooting, installation, and maintenance of data center client’s tools. Smart hands relate to an expert or a team of expert technicians positioned on-site that can speedily respond to problems that may go up within the data center. Smart hands are […]
Smart Hands Services: When Your Time is Worth Money

There comes the point in your company’s IT department when a task needs to be completed, and no one is available or able to handle it. Maybe it’s off-hours. The task can be small or major—basic diagnostics; plug in a cable; add IP addresses to a firewall. Regardless, no one is available. And the task […]
Managed vs. Unmanaged Servers: Which is Right for Your Business?

Getting a server for your business is a significant step, but a rewarding one. The ability to host your own site or store your private data onsite, along with uninterrupted access and analysis of trends, makes this a wise investment. However, one of the first decisions you will be required to confront is whether you […]
Why Does Your Business Environment Need Redundancy Solutions

Redundancies signify components that need backup. Examples of this can be failures in the Ethernet cable, power supplies shortages or networking card errors. If these backup components are in place, then your business can rest assured that it will not suffer in the event of the primary source fails. The backup components act as the […]
Micro Segmentation vs Endpoint Protection: What You Need to Know

When protecting endpoints from malware or any type of command and control based Malcode (malicious code), many different approaches and techniques are utilized by the software an organization or enterprise chooses to utilize in order to protect the machines in their environment. Different solutions to safeguard endpoints include on-site binary isolation, server-based micro-virtualization, real-time system-isolation, […]
Cryptographic Ransomware Removal And Protection With Volico Endpoint Protection
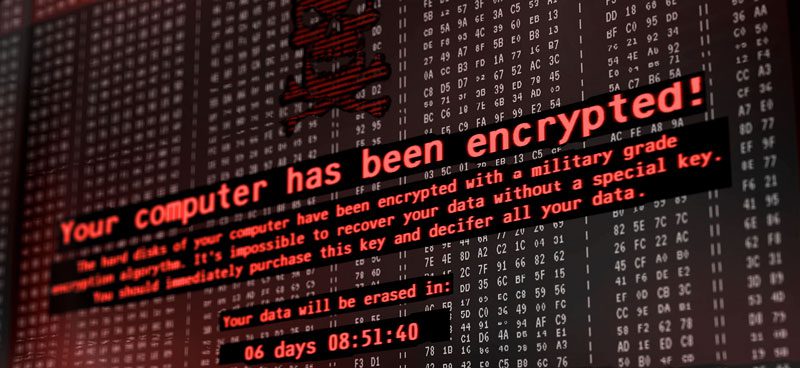
Crypto Ransomware is rampant. Most variants of it (CryptoLocker, TeslaCrypt) are malicious binary files that are very intelligent, aware of their surroundings, and highly polymorphic. Cryptographic ransomware that can morph on the fly makes it extremely difficult for standard signature-based antivirus programs to detect, as well as making it difficult to detect with “Anti-Malware” programs. […]


