Server Uptime: A Fundamental Business Issue
No IT service will ever try to claim that server downtime is acceptable, but many will claim all sorts of issues causing downtime are unavoidable. For businesses that rely more and more heavily on their web presence or web applications to do business, server uptime can be the difference between productivity, financial solvency—even industry presence—and […]
Ransomware as-a-Service (RaaS) Explained

Ransomware as-a-Service is making cyber crime all too easy. Now, criminals don’t have to create this malicious type of software. They can essentially use it for a minimal cost and pay the developers a cut, a percentage. Ransomware is computer software that criminals maliciously installed onto computers, cellphones, and other devices. The software typically enters […]
Managed Security Services: Service Provider Benefits

Business security needs can be a complex issue to tackle. Particularly for nontechnology-oriented businesses, the day-to-day burdens of cyber security, firewall management, malware avoidance, customer data security, intrusion detection, and more can be overwhelming or impossible. Many companies turn to a managed security service provider in order to ensure that these issues are addressed by […]
Firewalls: The Essential Buyer’s Guide

Firewalls help to protect computers, applications, and networks from external attacks. They are essentially security software that serves as the gatekeeper for networks, making sure that only authorized communication traffic is allowed to enter and leave. Most company networks begin as secure entities. Outside networks, such as the Internet, pose a risk to these company […]
Best Practices on How to Create a Reliable DR Strategy

Every company that relies on its information systems for daily operations and for customer relations needs to have a disaster recovery plan in place. The difference between a valid plan and no plan (or a bad plan) can mean the difference between staying in business or being out of business. Downtime losses for companies that […]
What to Do After a Data Breach

Data breaches occur in every type of industry – healthcare, retail, financial services, communications, and any business you can think of. Proper planning to avoid data breaches is always the first priority. The best way to respond to a breach is to make sure it doesn’t occur in the first place. Still, breaches do and […]
A Guide to a Successful Data Center Migration

Many businesses see value in migrating their technology to a third-party data center. Advantages can include financial savings, better performance, the ability to partner with other companies, expanding global reach, better customer satisfaction, and faster disaster recovery. Data migration requires a great deal of planning. The IT department of the company contracting with the data […]
How Hardware Load Balancers Help Manage Network Traffic
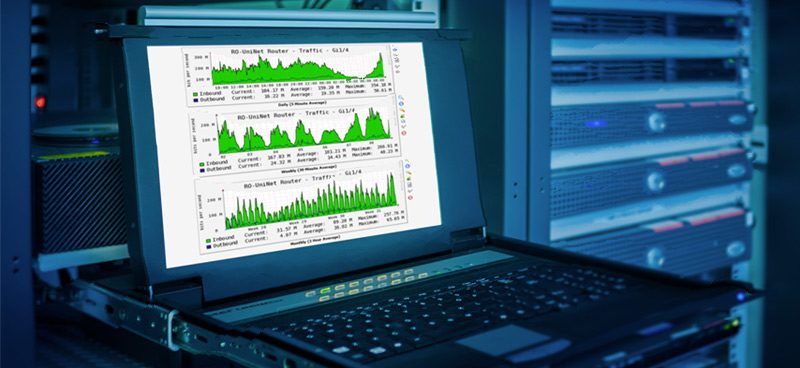
Computer networks are akin to railway traffic systems. They need to ensure that multiple trains (with multiple cars) using a small number of railway lines operate efficiently. Efficient operation means that that the trains don’t collide and that they reach their destinations on time. Computer traffic within or across networks must handle billions of bits […]
Why Managed Firewalls are an Incredibly Important Organizational Security

A managed firewall is used to protect networks from attacks, including both networks that connect to the Internet and internal company networks. The firewall acts as a sort of policeman; all messages that want to come in or leave the network first have to meet the firewall’s approval. Additionally, the firewall can control who has […]
Understanding the True Cost of Downtime to Your Business

Any interruption in computer information services can cause your organization large economic losses and loss of valuable human resources. This is true whether the interruption is due to poor computer software design, hardware malfunctions, fire or other destruction of buildings and equipment, or cyber-attacks. Every company and organization should anticipate business interruptions, have strategies to […]


