What You Need To Know About SolarWinds Orion Security Breach

Companies throughout the world use the latest technology and the internet to scale their businesses. The path to success is innovation and expansion; therefore, keeping up with the latest trends in terms of tech is going to make a massive difference down the road. Every successful company along the way had to build a solid […]
Understanding Enterprise Unified Threat Management (UTM) and Next-Generation Firewall (NGFW)

Network security now is the most important thing to have for all businesses, no matter it’s a small SMB or a complicated enterprise. While researching network security solutions, companies are coped with various options from a solutions point of view for dealing with every threat to the solutions which merge services into a single appliance. […]
Real-Time Server Monitoring Advantages and Benefits
As essential tools of the IT industry, both physical and cloud computing servers remain delicate, sometimes unpredictable, and often criminally underused. The data they generate, when collected and analyzed, can provide a wealth of useful information. However, server maintenance and data analysis both require dedicated monitoring, tracking, and storage. How can an IT manager balance those […]
Discover How Volico Can Protect Your Business Against Microsoft’s RDP BlueKeep Exploit

For the may 2019 security patch release, Microsoft included a patch for a RCE (remote command exec) bug in the remote desktop service (RDP). This was to fix an exploit where an unauthenticated attacker would send “core-system” malformed and malicious RDP messages to the target server using system-level message service to the MS_T120 protocol of […]
How to Select an MSSP Partner?

An MSSP (Managed Security Services Provider) Partner is chosen by organizations for several reasons like security, talent shortage, budget cuts and the complexity of trying to stay on top of fledgling threats arising in the world of tech. Here are five areas you need to focus on to select an MSSP partner. The following are […]
Vulnerability Assessment vs. Penetration Test
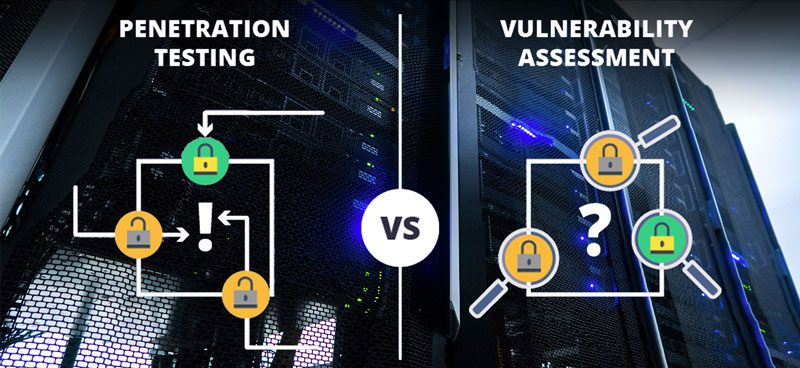
It is quite a common problem to pay for network penetration testing services and getting a hundred pages penetration testing report listing the vulnerabilities detected by a scanning tool. Vulnerability assessments are often offered in place of penetration tests. But what is the difference? Vulnerability Assessment A vulnerability assessment intends to identify certain weaknesses in […]
Why Are Cybercriminals Targeting Educational Institutions

Last year saw a sharp increase in the number and impact of cyber attacks on educational institutions across the US. While healthcare and financial industries have always been prime targets, cyber criminals seem to be turning more to learning institutions as targets for hacking. It is not just criminals prepared to sell your information on […]
Hosted Firewall vs. Managed Firewall

Firewalls are designed to protect your computer infrastructure (networks and computers) from malicious attacks. The firewalls control what information can go in and what data can go out. A firewall protection program can be installed on just one computer or on the server or routers that control the full network. There are different ways to […]
Managed Security Services: Service Provider Benefits

Business security needs can be a complex issue to tackle. Particularly for nontechnology-oriented businesses, the day-to-day burdens of cyber security, firewall management, malware avoidance, customer data security, intrusion detection, and more can be overwhelming or impossible. Many companies turn to a managed security service provider in order to ensure that these issues are addressed by […]
Internet of Things to Increase IT Security Needs

The Internet of Things (IoT) is constantly expanding. Experts believe that by 2020, 50 billion items will be part of the IOT. As expansion increases, connectivity issues increase exponentially because each object is capable of being connected with another object. These connections create ever-expanding networks with ever-expanding security concerns. IoT security: the problem The need […]


